How to Capture Data Changes in SAP Security Logs
How to Capture Data Changes in SAP Security Logs
Tracking data changes in SAP security logs is crucial for maintaining data integrity and ensuring compliance with regulatory standards. In this article, we will explore the most effective methods for capturing and analyzing data changes within SAP security logs.
Importance of Monitoring Data Changes in SAP Systems
SAP systems contain data spanning dozens of modules, thousands of tables, and millions of rows. SAP organizes this data systematically and module-wise. Besides logical classification, this data should also be categorized based on sensitivity from a security perspective. Below are some critical modules and examples of sensitive data associated with them:
HR (Human Resources)
- Sensitive Data:
- Employee Information: Basic details (e.g., PA0002 - Personal Data, PA0006 - Address Data)
- Salary and Payment Data:
- PA0008: Basic salary details (gross/net)
- PA0009: Bank account information (account number, IBAN, bank name)
- Additional Payments/Deductions: PA0014, PA0015 (special bonuses, deductions)
- Tax and Social Security Data: Tax class, social security numbers
- Performance and Disciplinary Records: Training, evaluations, and disciplinary actions
FI (Financial Accounting)
- Sensitive Data:
- Bank Transactions:
- Payment transactions and bank statements
- Customer and vendor banking details
- Invoices and Payments: I-AR (Accounts Receivable), FI-AP (Accounts Payable)
- Financial Reporting: Income and expense reports, balance sheet data
- Bank Transactions:
MM (Materials Management)
- Sensitive Data:
- Vendor Information:
- Banking details, pricing terms, contracts
- Material Movements:
- Inventory levels, purchase order details (PO documents)
- Pricing Information: Material price lists, cost records
- Vendor Information:
SD (Sales and Distribution)
- Sensitive Data:
- Customer Data:
- Billing addresses, contact details, payment history
- Sales Orders: Order contents, special discounts, customer contracts
- Revenue and Discount Data: Sales performance, customer loyalty analysis
- Customer Data:
PP (Production Planning)
- Sensitive Data:
- BOM - Bill of Materials
- Production Plans and Work Orders
- Capacity Planning and Costing Information
QM (Quality Management)
- Sensitive Data:
- Product test results and analysis reports
- Compliance documentation
A Brief Overview of Table Data Structure
In SAP security systems, it is essential to mention the concepts of Data Element and Domain when discussing data stored in tables. A typical table consists of fields, and each field is associated with a Data Element, which is an object containing properties such as data type and field label. A single Data Element can be used across multiple tables.
Additionally, a Data Element is linked to a Domain, which defines the data type (e.g., integer, string, char, datetime, etc.) and the field length. The Domain acts as a separate object that specifies these technical properties.
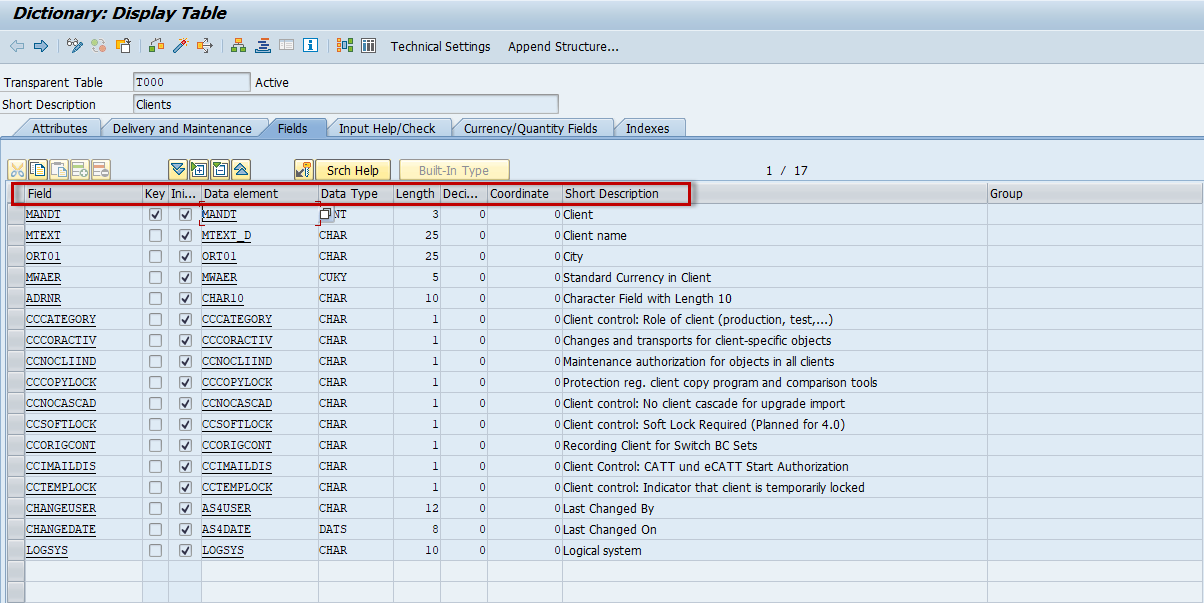 Figure 1: TABLO Structure
Figure 1: TABLO Structure
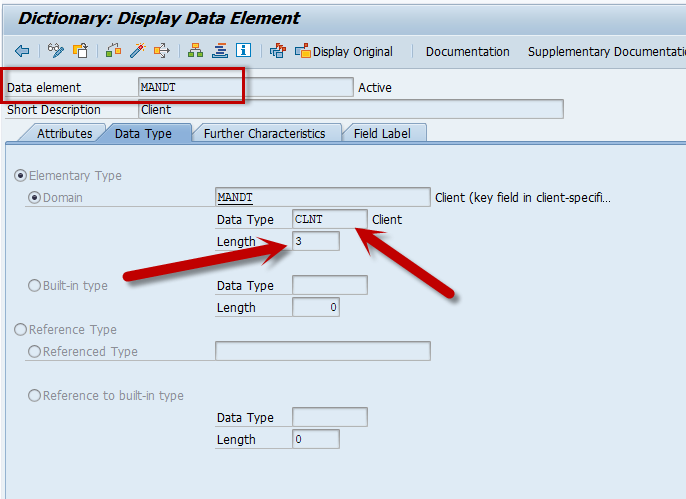 Figure 2: Data Element and Domain
Figure 2: Data Element and Domain
The frequency of modifications or new entries in SAP tables depends on their position within a specific module. Data stored in these tables may be updated frequently or infrequently. End-users and module experts commonly access this data for reporting purposes. All activities performed at the application level, such as updates, inserts, or data views, are recorded in the SAP logging system.
Access to tables at the application level can be observed in Security Audit Logs. For example, in the case below, the SE16 transaction code (used for table display) was utilized to access the PA0008 table (containing employee salary and payment details) in display mode.
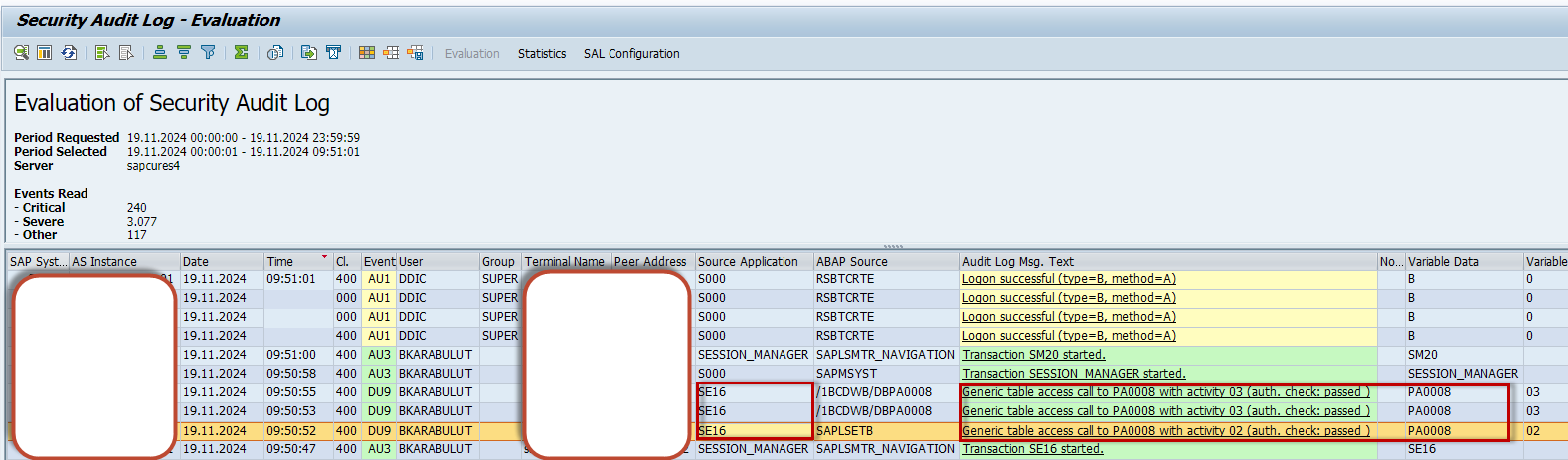 Figure 3: Security Audit Logs
Figure 3: Security Audit Logs
When table access is performed using configuration transactions like SCC4, logs are also created in the Security Audit Log (SAL). For instance, accessing the T000 table through SM30 using the SCC4 transaction code is logged and can be viewed using SM20.
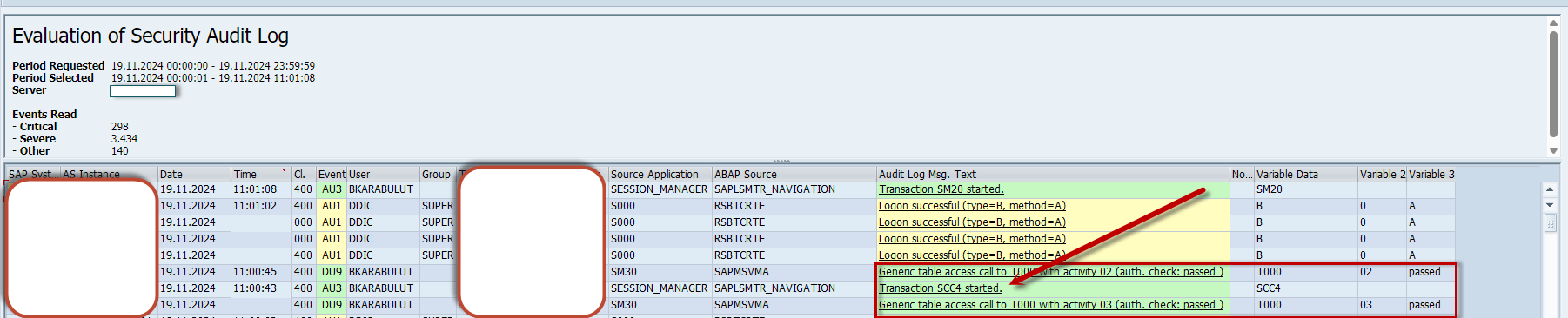 Figure 4: Security Audit Logs
Figure 4: Security Audit Logs
However, not every transaction code or report execution automatically generates such logs. For tables deemed critical by the customer, if no logs are being recorded, custom logs can be created using user exits and custom coding.
In custom programs (typically starting with Z or Y), developers can log table access or modification operations. This can be done either:
- Before a SQL query (e.g., SELECT, SELECT SINGLE)
- Before a COMMIT WORK operation
This approach ensures that all critical actions on tables are captured even when standard logging mechanisms are insufficient.
SAP General Log Types
Brief descriptions of some of the logs kept in SAP systems are as follows.
Security Audit Logs (SM20)
- Description: It is used to monitor user activities and security-related events.
- Sample Logged Data:
- Successful and unsuccessful login attempts
- User authorization changes
- Execution of critical transaction codes
System Logs (SM21)
- Description: It contains records of events that occur at the system level.
- Sample Logged Data:
- System errors and warnings
- Kernel messages and system states
- RFC connection errors
Application Logs (SLG1)
- Description: Stores logs of processes running at the application level.
- Sample Logged Data:
- Errors encountered in Application processes
- Transaction completion information (pass/failure)
- Detailed transaction records for specific business processes
Read Access Logs (RAL)
- Description: It is used to monitor their read access to sensitive data. It is especially critical for GDPR compliance.
- Sample Logged Data:
- Who accessed what sensitive data?
- Access timestamp and transaction details
Change Logs (Table Logging)
- Description: Logs changes made to table data.
- Examples of Logged Data:
- Data insertions, updates, or deletions at the table level
- Accessible primarily through the SUIM or SCU3 transactions
Transaction Logs (STAD)
- Description: Monitors performance and user activities for transaction codes.
- Examples of Logged Data:
- Transaction codes executed by users
- Processing time and resource utilization
Gateway Logs (SMGW)
- Description: Contains logs for connections made through the SAP Gateway.
- Examples of Logged Data:
- Connections established with external systems
- Connection errors and their statuses
HTTP Logs (SICF Logs)
- Description: Logs calls and access made through SAP's HTTP services.
- Examples of Logged Data:
- Web-based access made by users
- Web service calls and related errors
Job Logs (SM37)
- Description: Provides details about background processes (jobs).
- Examples of Logged Data:
- Completion status of jobs (successful/failed)
- Errors and warnings encountered during job execution
Integration Logs (PI/PO Monitoring)
- Description: Monitors integration processes in SAP PI/PO (Process Integration/Orchestration) systems.
- Examples of Logged Data:
- Message delivery and transformation errors
- Message statuses (success/failure)
Database Logs
- Description: Tracks events occurring at the database level.
- Examples of Logged Data:
- Database errors and performance issues
- Transaction commit/rollback events
HANA Audit Logs (via HANA Studio)
- Description: Logs activities occurring in the SAP HANA database.
- Examples of Logged Data:
- Activities performed by database users
- Authorization checks and access controls
Workflow Logs (SWIA, SWI6)
- Description: Provides detailed logs for SAP Workflow processes.
- Examples of Logged Data:
- Workflow steps and their completion statuses
- Which user completed which step
Transport Logs (STMS)
- Description: Contains logs related to transport operations.
- Examples of Logged Data:
- Import/export details of transport packages
- Errors encountered during transport operations
Each of these logs serves a specific purpose and plays a critical role in ensuring the security and performance of SAP systems. Regular monitoring of these logs is essential to maintain system integrity and compliance with organizational and regulatory requirements.
Storing Logs for Changes in Critical Tables
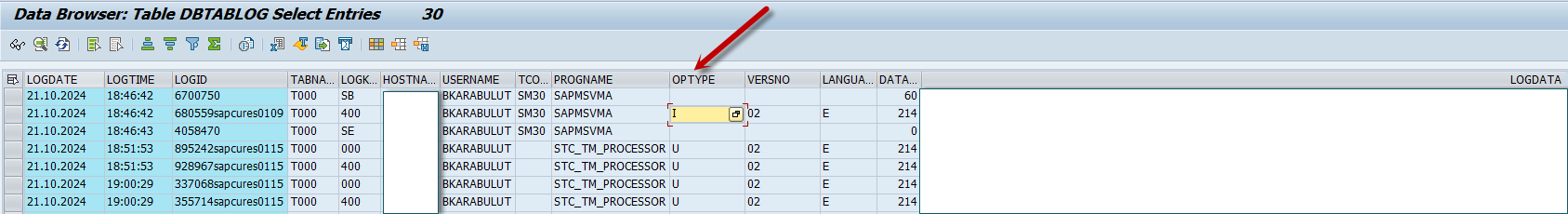
By default, SAP enables logging for critical tables during system installation. The records created from this logging are stored in the DBTABLOG table, which raises the question: How to capture data changes in SAP Security Audit Log? This table reflects events such as insert, update, and delete operations performed on critical tables.
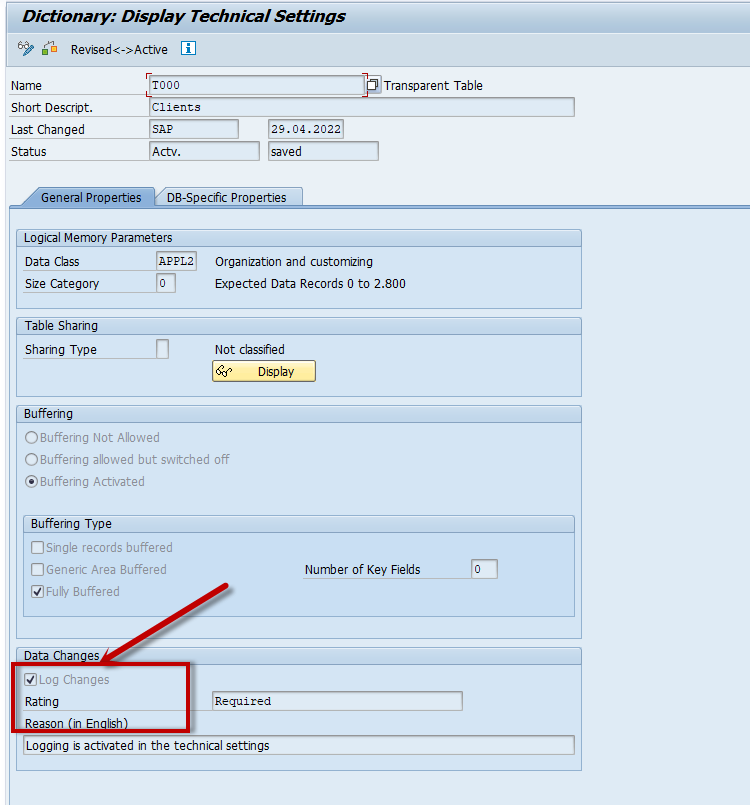
For tables outside the default logging scope, logging can be manually activated as follows:
- Navigate to Transaction Code SE11
- Enter the Table Name and select Display
- Go to Technical Settings
- In the Data Changes section, check the box labeled Log Changes
Once this setting is activated, records for changes in the specified table will be logged in DBTABLOG.
It is essential to archive the data collected in DBTABLOG at regular intervals. Over time, the volume of log entries can grow significantly, potentially impacting the performance and storage capacity of the database. Proper archiving ensures efficient system operation while retaining critical change records for auditing and analysis.
 The OPTYPE field in DBTABLOG shows the SQL operation (UPDATE, DELETE, INSERT)
The OPTYPE field in DBTABLOG shows the SQL operation (UPDATE, DELETE, INSERT)
RAL (Read Access Logs)
SAP RAL (Read Access Logging) is a mechanism used in SAP systems to monitor and record user access to sensitive data. This feature is crucial for ensuring the protection of sensitive data under regulations such as GDPR (General Data Protection Regulation).
Key Features of RAL
- Monitors user access to specific data objects
- Logs queries or read operations on sensitive data
- Reports which user accessed which data, when, and through which operation
- Can be customized for targeted data fields and operations
RAL Configuration
- Activating RAL
- Run the /nRALMANAGER opcode through the SAP GUI
- Set the RAL Status option to Active
- Creating Logging Profiles
Define logging profiles to specify which operations and data to monitor:
Profile Creation:
- Go to the Profiles tab in the RAL Manager
- Click Create and enter a profile name
Defining Target Objects:
- Select the SAP data objects to be monitored (e.g., personal data, customer information)
- Specify the data types (table, field, or object) and the operations to be monitored
- Defining Rules
- Add rules to govern logging:
- Create rules at the profile level
- Customize rules for specific user groups, roles, or operations
- Storing Logs
- RAL logs are managed automatically in a database table
- Older logs can be archived using SAP's standard archiving methods
- Testing and Validation
- Test the created profiles by having a user access sensitive data
- Verify that the relevant access logs are recorded correctly
- Reporting and Analysis
- Access the logs via SAP GUI or Fiori Launchpad
- Use the reporting tools in RAL Manager for detailed analysis
Important Notes
- Performance Impact: Activating RAL may slightly impact system performance. Focus logging only on critical data to mitigate this.
- Data Security: Logs may contain sensitive data, so proper authorization controls must be implemented.
- Compatibility: RAL is available for SAP NetWeaver 7.4 and later versions.
This configuration allows organizations to meet compliance requirements while ensuring that sensitive data access is monitored effectively.
Contact us to learn more and schedule a free demo of our product that detects security vulnerabilities in SAP systems. Ensure your systems are not only functional but also secure.
SAP Security Analyst: Role, Responsibilities, and Key Insights
SAP Security Analyst – Strengthen security, manage risks, and protect SAP systems from cyber threats. Roles, responsibilities, and best practices inside!
Which SAP Security Certification is in Most Demand 2025
Which SAP Security Certification is in Most Demand 2025
SAP ABAP Program Authorization Group Table
Explore the significance of SAP ABAP program authorization groups in managing access control and enhancing security within your organization.
SAP Security: A Guide to Secure and Compliant Systems
Unlock the secrets to SAP security with our ultimate guide, exploring best practices for protecting sensitive data, ensuring compliance, and enhancing business operations.
Analysis of Security Audit Log in SAP
Explore the importance of SAP Security Audit Logs in enhancing the security of your SAP environment.
SAP Audit Event Type Codes for Data Updates
Learn how SAP audit event type codes for updates enhance accountability, data integrity, confidentiality, availability, and compliance.
Listing of SAP Open Ports: A Comprehensive Guide
Learn how to check and monitor SAP system ports using various methods including sapcontrol commands, OS-level tools, SAP GUI, and Python scripting.
Authorization Objects in SAP Systems
Explore the importance of authorization objects in SAP systems and understand the critical tables that play a key role in SAP security.
Getting Files from Local PC via SAP GUI with Illegal Methods
Learn how to retrieve local files from a user's desktop using SAP GUI in SAP systems and understand the potential security risks involved.
SAP GUI Versions From a Security Perspective
Understand the importance of keeping SAP GUI versions updated for security and how to plan upgrades effectively.
The Concept of Parameters in SAP Systems
Understand the different types of profile files and system parameters in SAP systems, and learn how DefenceMore's One Click Audit can help ensure their security.
Critical SAP Vulnerability: CVE-2023-40309
Learn about the critical CVE-2023-40309 vulnerability in SAP systems, its impact, and the corrective steps to secure your environment.
Are Your Systems Really Secure?
Discover the vulnerabilities in your SAP systems and learn about DefenceMore's One Click Audit for SAP Systems.